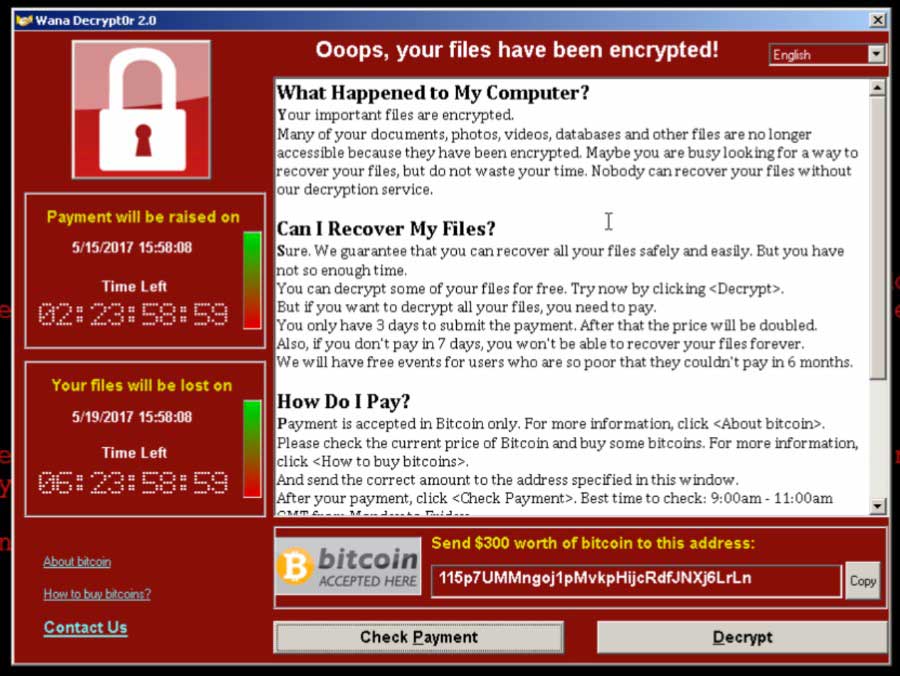
How to ensure that WannaCry or any ransomware never cripples your business
Image Credit: Talos
By now, most people will have heard about the infamous piece of ransomware known as WannaCry/WannaCrypt. If you and your company have been lucky enough to avoid it so far, read on to make sure you you’re ready for this sort of malware in the future.
First, what is ransomware?
In case you’re not sure what ransomware is, the term ransomware refers to a category of malware in which the malware encrypts all the data on your device, making your files unusable by an app, and demands a ransom (hence the name) in order to decrypt your data. If you don’t pay the ransom, all your data will be permanently deleted after a short window of time.
Ransomware is a piece of malware which encrypts all your data and makes it unusable.
How can ransomware do such things, you ask? A piece of ransomware is able to access all your data by exploiting a flaw in an operating system, such as Windows in this case. If the security flaw is sufficiently compromising, it allows the ransomware to have full access to your files.
But how does the ransomware suddenly get access to your computer? There are several ways malware can get on your system. The most common and devious method is through opening an legitimate-looking email (when it’s actually not), and downloading an attachment contained in it.
Someone opens a malicious email, they get infected, then all other computers on the same office network get infected.
So if you’re a smart user and you always double-check the email sender and you never visit any suspicious/infected websites, you should be all good, right? Wrong! Being deceived by an email or downloading something from an infected website might be the most common mistakes people make that result in getting malware on their machines. But you don’t even have to make any mistakes to get your computer infected. If you work in an office, it only takes one colleague who makes that mistake on your behalf to allow the ransomware to replicate itself from the infected computer to all the computers connected to the same office network. This is possible because internal office networks assume it’s ok to receive files from other computers at the office. That’s exactly why WannaCry has infected hundreds of thousands of computers all over the world.
How serious is it?
Now that we’ve established how it all happens, the question is how do we get out of this mess? The answer, troubling as it may be, is that you will actually have to pay the ransom if you ever wish to see your documents and files again. After all, encryption is used for a reason: the person who encrypts data should be the only who who can decrypt it and use it. The twist in this case is that rather the owner of the data performing the encryption in order to secure it, the data is being encrypted by a malicious third party in order to hold it hostage for a ransom.
The person who encrypts data is the only who who can decrypt it and use it, whether that’s an attacker or a normal user.
That is why ransomware is considered such a disastrous piece of malware. People pay because the alternative of losing all their data is just not an option. Ransomware victims range from individuals, to small & big offices, government entities such Swansea’s police department in Wales, and even the UK’s National Health Service (NHS). Even more troubling, there isn’t a guarantee that the data will be unlocked after the affected victim pays the demanded ransom. It is completely up to to the attackers.
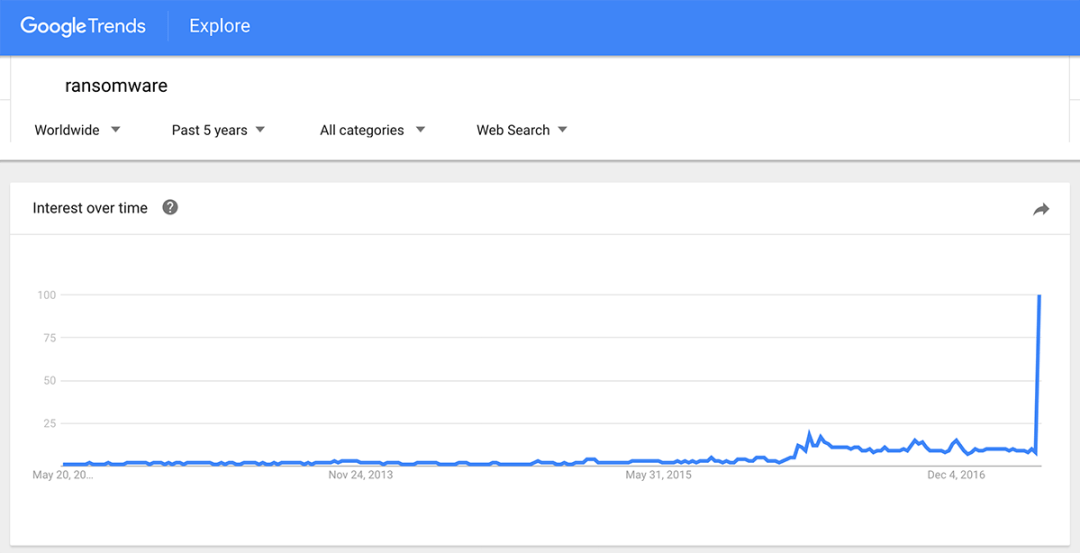
The bad news is not over. Because although this particular ransomware has already been shut down, you can be sure many more like it will surface in the near future. The notoriety of ransomware is only increasing. Just look at the Google Trends chart of the past 5 years. It started to pick up steam in 2016 before its meteoric rise in 2017.
How do we deal with the situation?
Security Updates Are Not A Joke
If you’re a good citizen and you have automatic security updates turned on in your device settings, then you are already much more secure than most other people. In fact, the security update that fixes the security hole exploited by WannaCry has been out for months, a long time before WannaCry became a news item.
If your automatic updates are on, you’ll avoid the vast majority of security threats.
Do yourself and your company a service, and make sure you have automatic security updates turned on for all your devices. If you’re not sure how to do that, ask IT for help or just Google it; it’s very easy. Remember that your oversight to do so won’t just affect you, but all the devices at your office. Trust me, you don’t want to be the reason your whole office is completely crippled by ransomware. By the same token, you should do your best to make sure your colleagues do the same because you don’t want their mistakes to result in your devices getting infected.
Backups Are No Joke Either
Security updates are not enough though. Because although in the case WannaCry, the security update came out early enough to protect people who updated, there have been and will be times when the malware will use an un-patched security hole, and if it gets to your devices, they will be completely defenseless.
Having only one copy of your data is a matter of time before losing all your data.
But rather than losing all your data, you should have regular backups of your devices. At any point in time, you should have at least 2 copies of all your data, so that in the event of a catastrophic event, you still have another full copy of everything you need rather than being left with nothing. Always assume that one of your copies will somehow get destroyed, whether it’s malware, some stealing your device, water damage, hard drive failure, and or whatever it may be. By that logic, having your data in one place only with no other copies is only a matter of time before you’re left with no data at all. That is philosophy behind two is one, one is none.
Security By Design
All that said, we know that most people won’t do backups, even you, dear reader. We should feel lucky enough if most people make the effort to flip on the switch for automatic security updates, but that’s about as much effort as we can expect people.
Asking people to do the best thing is rarely a reliable strategy for getting things done, even if it’s for their own good. How many of us never eat fast food, exercise regularly, sleep 8 hours a day, remove distracting apps from our phones? Exactly.
A better approach would be to circumvent the issue at a much earlier stage. How? By making the effect of computer data loss almost meaningless. Of course, when I say ‘computer data loss’, I mean documents and files that stored locally on your computer. What’s the alternative then? Two words: The Cloud.
Adopting a cloud-first mindset will turn ransomware attacks from a disaster to a minor nuisance.
Having a cloud-based workflow will save you from the headaches of computer data loss. For example, if all your documents are stored in a cloud environment such as G Suite (Google Docs, Sheets, & Slides), you wouldn’t lose a byte of data even if your computer is completely and utterly fried! All you’d need to do is remove the malware and go back to business as usual because no malware can get into Google’s servers and hold your data hostage. Similarly, if your company’s customer databases and interactions are stored in the cloud on a platform like Salesforce, you wouldn’t have to rely on a local company server that could just as easily be compromised or struck by natural disasters as your laptop.
Cloud providers (such as G Suite and Salesforce) do the hard work on your behalf of making sure no ransomware ever gets into their servers, and they backup your data on secure servers in multiple locations so you never have to worry about accessing it.
Closing Thoughts
No matter which of these solutions you choose, I urge you to choose at least one. Do something. Any of the suggestions above will help to severely limit the amount of damage caused by ransomware and other types of malware. I promise you that taking action now will fill you with a sense of relief in the near future when another security breach strikes the world again soon, and you see people and companies all over the world scrambling to do something about it when it’s probably too late already.
About Lava Protocols
A leading Salesforce & G Suite Partner based in Malaysia, Lava Protocols has a widespread clientele that spans across 7 countries within the region. Lava is an authorised Salesforce Partner & Google Partner in Malaysia and has more than 10 years of cloud solutions and consultation experience. We pride ourselves in not just being a Salesforce Partner & Google partner but in also understanding the needs of our customers and taking their business to the next level.